


I recently had the opportunity to sit in on a conference call with the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) and got a chance to hear how they’re thinking about protecting against cyber threats after escalating tensions between the US and Iran.
I’d like to summarize what I heard and reference a few useful supporting cybersecurity guidelines.
On the call CISA made it clear that although they’ve prepared a National Cyber Awareness System Alert and a CISA Insights document specific to the increased geopolitical tensions and threats, they have yet not seen an increase in attacks from Iran.
Read more >>

In today's post, I'd like to introduce you to Loren Kohnfelder, an old friend of mine. I met Loren at Microsoft in the late 90's when we were tasked with the herculean task of improving the security of Internet Explorer.
It was an exciting and harrowing time, and while it is amazing to think about how far we've all come, it is also surprising to realize how many of the security challenges we struggled with twenty years ago are still with us today.
Read more >>

I caught three of my fingers in a tablesaw this last weekend, which caused a severe hand injury, mangling my fingers, tearing off my fingernails, and breaking the bones. It was pretty terrible, but luckily the hand surgeon says I should have a complete recovery in a few months.
Me being me, this got me thinking about some of the things that I could’ve done to mitigate the injury before it happened.
Read more >>

A friend of mine just left the world of consulting. I asked him for the biggest change in his thinking, he said:
Something is going to go wrong. It’s not a matter of if, it’s when. When that bad thing goes wrong everything hinges on how you detect and respond to it.
As consultants so much of our job is focused on reducing risk for our clients, but that’s all we can do.
Read more >>

I used to think I’d like to be a CISO. Now that I’ve spent the past few years speaking with CISOs, I’m not so sure I’d want the job. CISOs have targets on their backs, they hold our data in their hands and I, for one, am thankful for what they do.
I’m convinced that the CISO job is one of the hardest, most thankless, and most stressful jobs on the planet.
Read more >>
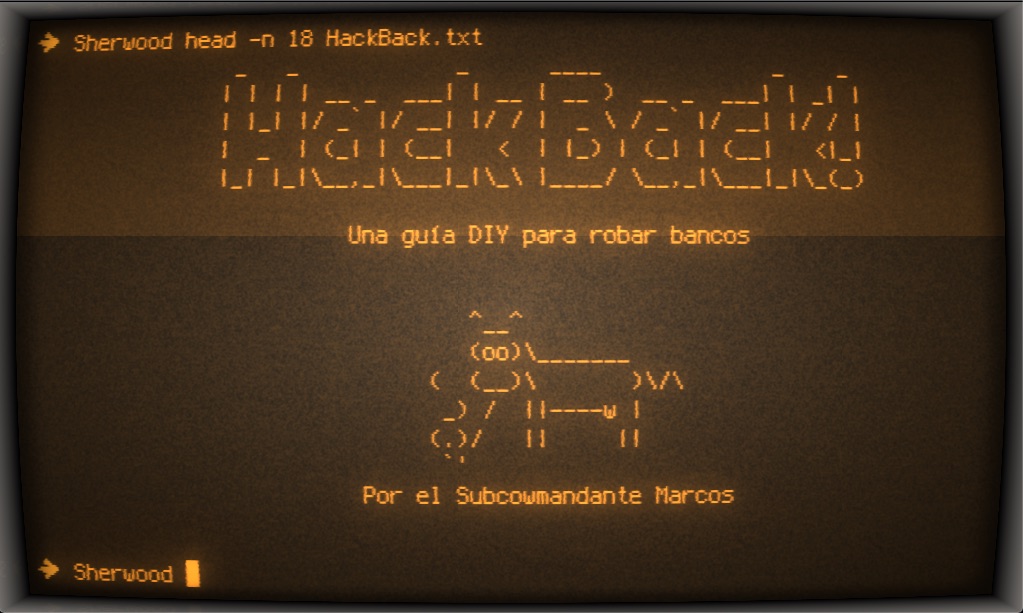
On Saturday a transparency collective named “Distributed Denial of Secrets” tweeted that they have released a massive data set from a recent breach. Over 2 terabytes of data has been released and is hosted by DDoS and on Torrents. In addition to the data that was released the hacker published a manifesto and hacking guide called “HackBack - A DIY Guide to rob banks" alongside the data dump. The hacker, who goes by Phineas Fisher, originally wrote the HackBack guide in Spanish, however, this morning I found a translated copy.
Read more >>
The Next Wave of Cyber Attack Imagine receiving an email with your username and password as the subject line. Inside the email there is a PDF that has been encrypted with a password provided in the body of the email. What do you do? Whoever sent the email has already proven they know who you are, and you probably want to know what else they have and what they’re asking for, right?
Read more >>

… or not enough, but you certainly don’t have it right.
Security takes commitment, but it’s not as simple as all or nothing. Knowing how much to commit for your level of risk tolerance is critical. The first thing you need to do when improving your security program is set honest goals about what you want to achieve.
Ideal security investment means, do what is necessary and nothing more. Every dollar you spend to secure something that isn’t going to be attacked is a dollar that isn’t used to lead the market, build new features, or sell and market your solutions.
Read more >>

In my last post , I talked about the fact that none of us knows how to solve the problem of cybersecurity. It’s a tautology, so it shouldn’t be surprising. If we knew how to solve the problem, the problem would be solved. Therefore we don’t know how to solve the problem. But it is surprising, and so it feels like a ‘hard truth’ rather than ‘the truth’.
When confronted with a long-standing problem (like cybersecurity), it is typical to assume that if we had more will, more resources, more intelligence, or perhaps more of all of the above, we could solve the problem.
Read more >>

I want to let you in on a little secret. Nobody in the security profession, especially those of us in the software security profession, truly knows what we are doing. You’d never know it talking to security vendors. If you attend a security conference you can walk the booths and talk to hundreds of security professionals selling solutions that cost tens or hundreds of thousands of dollars, each promising that they will solve your security problems with their technology platform, their professional services, and most importantly with their new deep learning, AI algorithms.
Read more >>