The best way to understand attacker tools, data breaches, and the underground marketplaces is to go to the source and learn what we can. Join me on a tour of the Darkweb.
Warning: the following action should be performed by trained professionals only. Do not attempt this at home.
One of the great benefits of large scale network connected computers is that it allows likeminded people to build communities in order to share ideas, techniques, tools, and software. These capabilities have been a powerful instrument in effecting political and social change. In the same way, though, it can be used to help illegal or problematic groups to organize. Once connected, members can undertake some of society’s worst activities, including buying and selling stolen data, illicit goods, and coordinating illegal real-world activities such as human trafficking.
In order to combat these things we must understand their systems, technologies and methods. In this article I’ll be walking you through a tour of the dark web. We will explore the tools and some of the websites available as well as what makes these technologies interesting from a technology perspective.
The dark web is built on suite of impressive technologies:
- Tor is a sophisticated use of three layers of encryption which allows a user to hide their location and destination from third parties sniffing the network.
- Riffle uses a novel shuffle algorithm to address the same challenges as Tor with a lower latency.
- VPNs are used to encrypt and tunnel network traffic from one place to another.
- Peer to Peer (P2P) communication technologies forego centralized server architecture which allows users to connect directly to one another. This makes centralized man-in-the-middle attacks more difficult.
All of these technologies address real concerns about privacy, anonymity, and security on the Internet, which was not developed with these values in mind at its ordination more than 50 years ago.
Tor has been used to help users organize, educate, or communicate under the watch of oppressive governments. P2P technologies speed up the download of large files and reduce single points of failure. VPNs are used by both corporations and end users to protect privacy and security on hostile networks.
However, it’s critical to understand how these are also being used by criminal elements in order to protect ourselves and our communities from dangerous behavior.
The Darkweb is roughly defined as an overlay of barely visible networks that exist on the Internet. These networks require specific software (such as Tor, VPN or a Usenet clients) and authorization to access. They are often not indexed by search engines and rely on word of mouth or directories of listings. The Darkweb is not the same as the Deepweb, which is simply unlisted websites.
In this article I’m going to focus on one aspect of the Darkweb, Tor, The Tor Web Browser, .onion websites, and how to navigate these networks. As mentioned above there are multiple other aspects of the Darkweb, giving a complete picture of the Darkweb is impossible, so this will be a starting off point.
To get started we will install the Tor Browser . Tor is a networking protocol, and the Tor Browser makes the connection, negotiation and browsing of encrypted networks easy. Websites on Tor use .onion as their TLD. One popular listing site is dark.fail. It is available both on the public internet at dark.fail or http://darkfailllnkf4vf.onion/ on Tor. Like many listings on the DarkWeb it is simply just a listing of URLs. In order to protect against clearnet (not Tor) DNS attacks the links aren’t even live. You have to copy and paste them into your URL bar yourself.
Each of the sites is an exchange for goods, services, or information. Many require you to register, although none that I’ve seen require valid or official credentials and none verify your real name. I have noticed that the URLs and sites aren’t predictably reliable. The URLs change often and the sites may go up or down. That’s part of the excitement of the Darknet, I suppose. Once you’ve picked a site the registration and browsing is the same as any other website, albeit slower. Kind of like browsing the web in the 90’s. I really appreciate the dedication to security and privacy the you find on the Darkweb. It’s almost ironic that the security and privacy controls are better here than anywhere else I’ve seen on the web. I see frequent reminders about phishing, to enable 2FA, and to rotate passwords and pins.
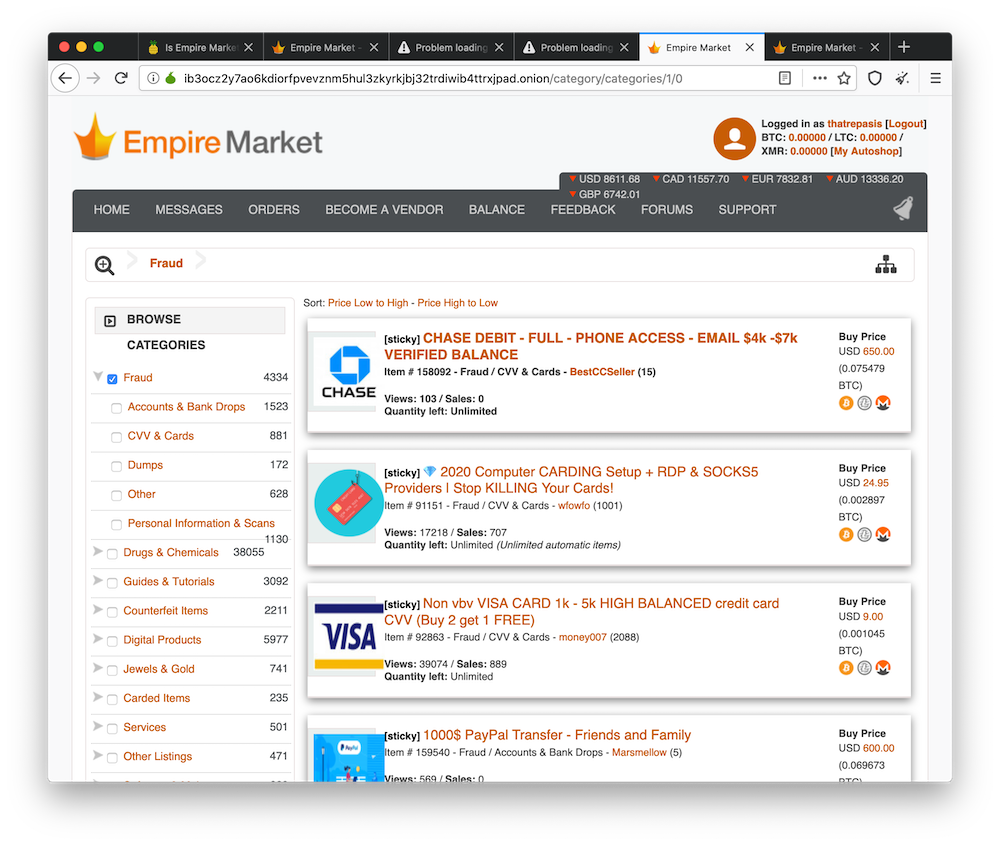
Exploring one of the more popular marketplaces you can quickly see the impact of data breaches. As Jason mentioned earlier it’s often the case that an identify or account is worth more on the black market than it is to the company charged with protecting it. That’s clear after browsing the “fraud” category on Empire Market. In this case they even walk the buyer through the process of performing a SIM spoofing attack with the information provided (Full name, DOB, Full SSN, Balance, Card number, PIN, CC exp, CVV, Billing address, Phone number, email address, PHONE PIN, PHONE ACCOUNT NUMBER). The price per account varies from $650 for an account with $4-7k available to $1000 for an account with $15-$20k available. Another listing offers quick methods to verify stolen cards, while others sell older accounts or credentials for cheaper.
Of course digital and fraud related products aren’t all you can buy and sell on such a market. Remote Access Tools, malware, ransomware, and hackers for hire are just clicks away.
I found browsing through these listings to be eye opening. It really hammered home how important it is for us to protect the data we are given by our customers. The risk is very real, the attackers have amazing access to the tools and data they need to steal your data, and the entrepreneurial zeal to sell it and ensure their customers get maximum value from their purchase.
